
Learn how to detect and respond to SSH brute-force attacks using Wazuh SIEM. This guide covers setting up rules, monitoring logs, and generating alerts to enhance your server’s security.
Machines Used:
- Ubuntu with Wazuh installed (Server)
- Ubuntu with Wazuh agent installed (Client)
- Kali Linux (Attacker)
Configuration for monitoring the Auth log files
To monitor the auth logs of a client, configure the Wazuh agent ossec.conf file on Linux (Ubuntu) endpoint
- Edit the Wazuh agent configuration file.
sudo nano /var/ossec/etc/ossec.conf- Add the following lines between <ossec_config> tags in the config file.
<localfile>
<location>/var/log/auth.log</location>
<log_format>syslog</log_format>
</localfile>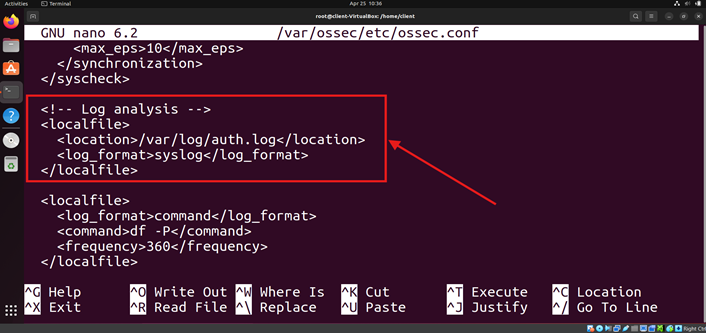
- Restart the Wazuh agent.
sudo systemctl restart wazuh-agentSetting up an SSH server
- Installing OpenSSH using apt.
sudo apt install openssh-server- Enable and start SSH.
sudo systemctl enable ssh
sudo systemctl start ssh- Go to the attacker machine and check if SSH is working.
ssh user@ipAccept the fingerprint and enter the password.
Configuring wazuh Active response capabilities
We are configuring Wazuh to drop the brute force requests and block the requests for a certain period.
- Log in to the Wazuh dashboard.
- Click on menu -> server management -> settings.
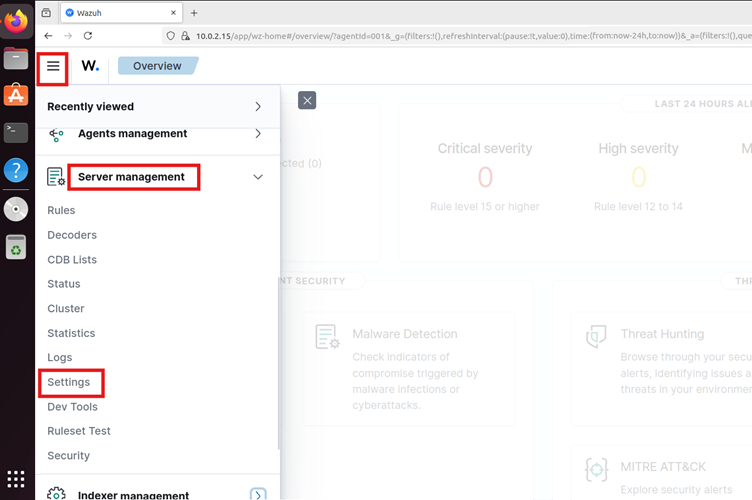
- Click on edit configuration.

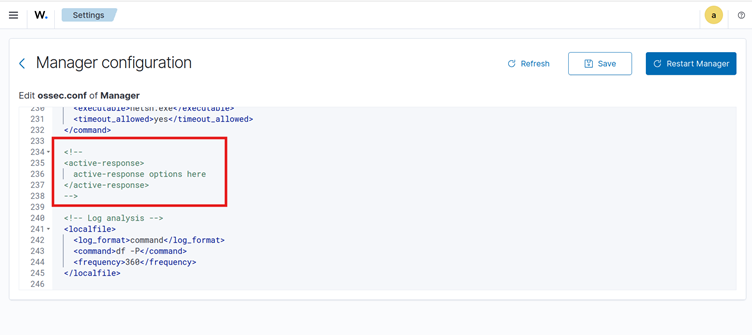
- In the manager configuration, look for this block
<!--
<active-response>
active-response options here
</active-response>
-->
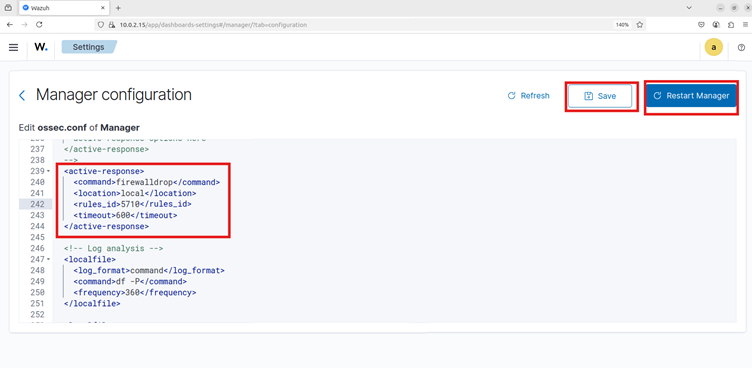
- Add this under the above block to configure the active response.
<active-response>
<command>firewall-drop</command>
<location>local</location>
<rules_id>5710</rules_id>
<timeout>600</timeout> <!-- Block IP for 10 minutes -->
</active-response>Rule ID 5710: Attempt to log in using a non-existent user
- Click save, and restart the manager.
Attack simulation
- Start the Kali machine for attacking.
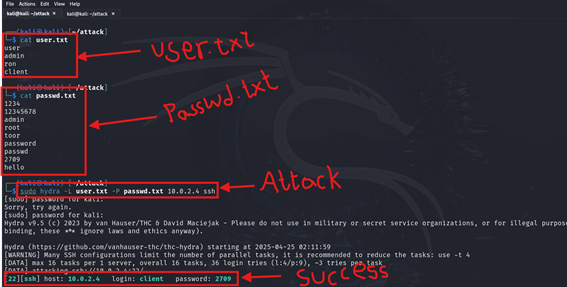
- Download or create common usernames and password files. Add the username and password of the client machine to the respective files.
- Run the following command to start the attack.
sudo hydra -L <USER_LIST.txt> -P <PASSWD_LIST.txt> <IP> sshThe following image shows the usernames and passwords, as well as a successful SSH brute force attack.
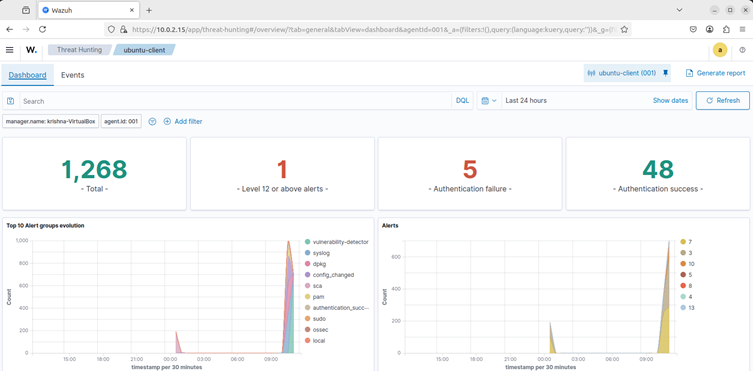
This is the screenshot of the Wazuh dashboard before the attack, which shows 5 authentication failures.
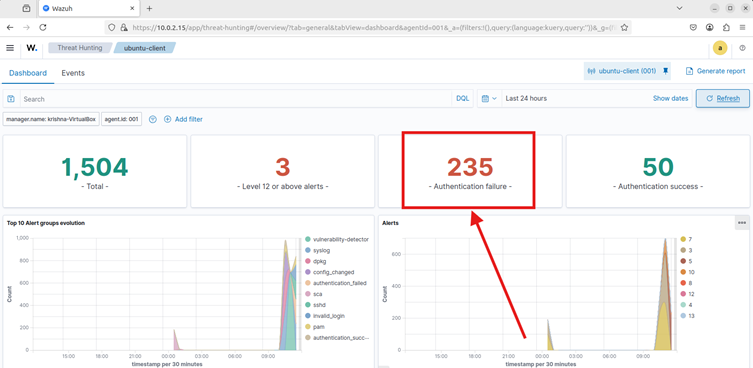
This is the screenshot of the Wazuh dashboard before the attack, which shows 235 authentication failures.
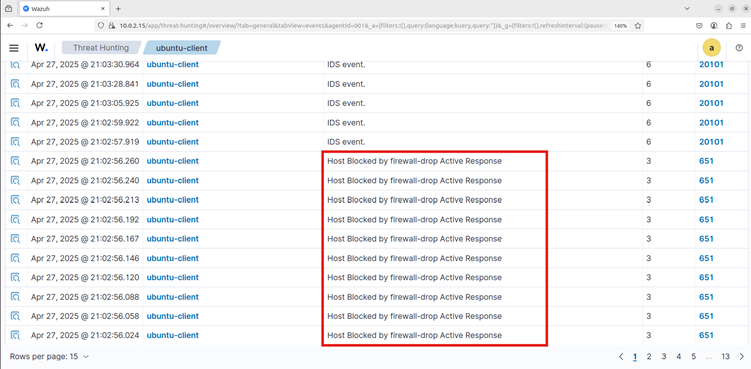
Now, if you try to log in using SSH, you cannot access for 10 minutes.
Visualization of alerts
To visualise the alerts in the Wazuh dashboard, go to Threat Hunting and search for the following filter in the search bar.
rule.id:(5551 OR 5712) We can also search for other login-related rules, such as 5710, 5711, 5716, 5720, 5503, 5504.
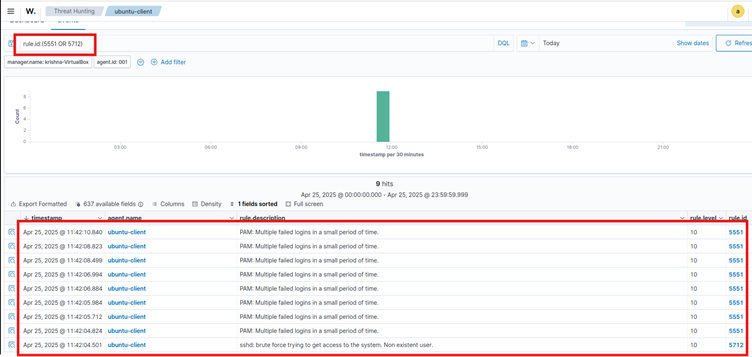
To visualize the alerts in the Wazuh dashboard, go to Threat Hunting, and the following alerts are generated.
Check out the GitHub link for the PDF. Click here
References
RELATED POSTS
View all


